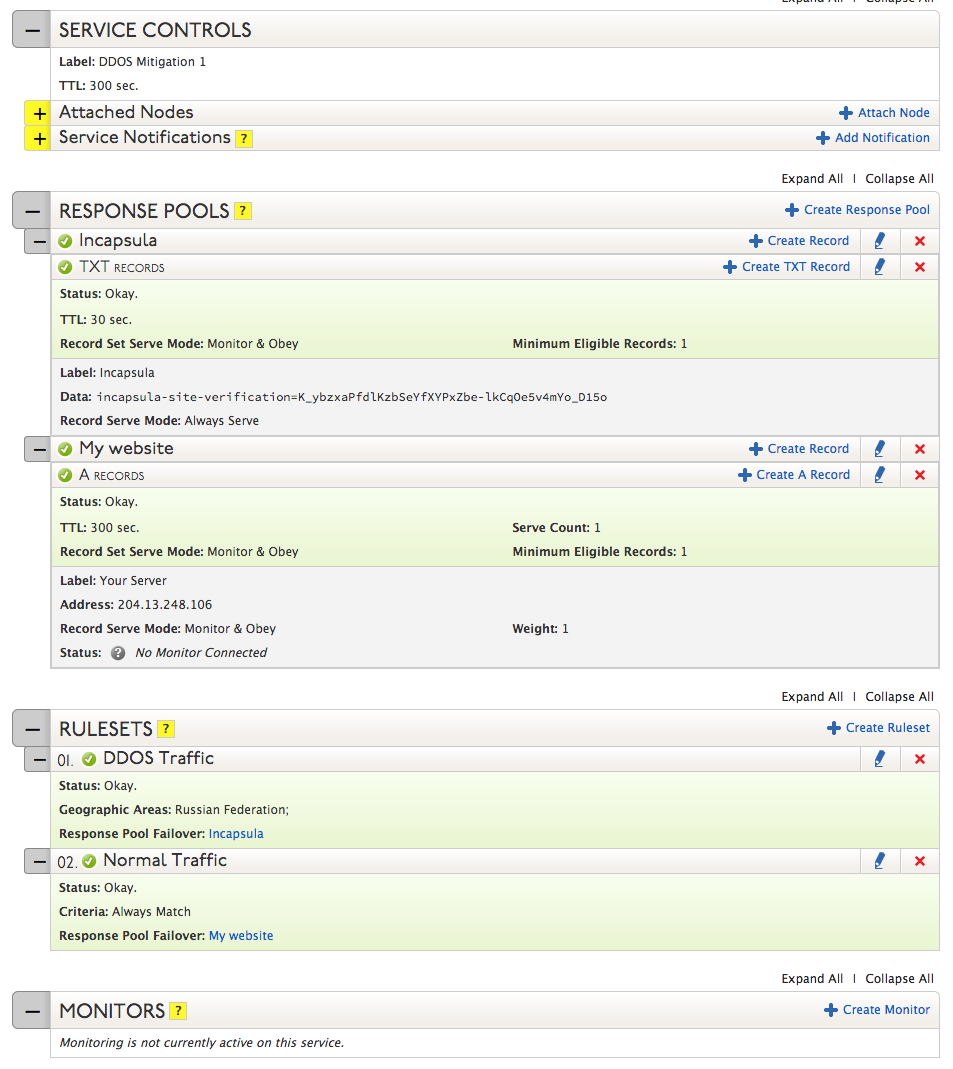
DDOS attacks often originate from specific regions around the world and many websites will use a DDOS mitigation service to filter out the bad traffic from their normal traffic. But DDOS mitigation service often charge by the amount of traffic they are receiving from your website, normal or bad. Using Traffic Director, you can alleviate some of those mitigation costs by only sending the traffic from a specific region (where the DDOS attack is originating from) to your mitigation service.
EXAMPLE: If your website is being DDOS attacked by bad actors in Russia, and you use a DDOS mitigation service like Incapsula, instead of sending all of your traffic through Incapsula, you can redirect only traffic from Russia to Incapsula using Traffic Director, and allow the rest of the world to access your site as normal.
In this article, we are going to set up two Response Pools, and their corresponding Rule Sets, with Traffic Director to do exactly this.
| 1. Log into your Dyn Managed DNS account. | |
| 2. Click Manage beside the zone you wish to add the Traffic Director service. | |
| 3. Select Traffic Director from the Add a New Service drop-down menu. |  |
| 4. Enter a label. This will help you identify this specific instance of Traffic Director in your zone. |  |
| 5. Click Create Service. | |
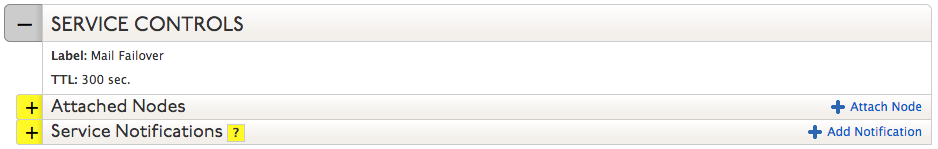
| 6. Under Service Controls, you can alter the default Time To Live (TTL) for this instance of Traffic Director or edit the label you created in the prior step.
Additionally, you can attach more nodes (zones or cut zones) to this specific instance of Traffic Director and be alerted of any changes to this configuration by adding a notifier in the Service Notifications section. Click Save. |
 |
| 7. Response Pools are where you can create groups of records you want to be served. In this scenario, we will be creating Response Pools for each your Website Traffic and the DDOS traffic. Click Create Response Pool and enter a label, “DDOS Traffic”.
Click Save. |
|
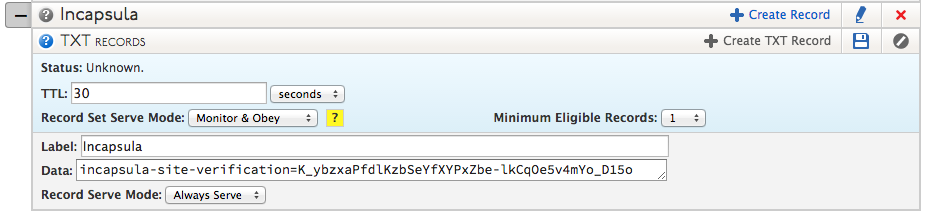
| 8. Click Create Record under your newly created Response Pool and then select A from the drop-down menu and add the mitigator’s IP address into the Address field.
Note: The records required for other DDOS mitigation services may vary. Reference their documentation to see what types of records are required for your mitigation service’s setup.
Click Save. |
 |
| 9. Repeat steps 7 and 8 to create a Response Pool for your Normal Traffic with an A record pointing to your website.
Click Save. |
|
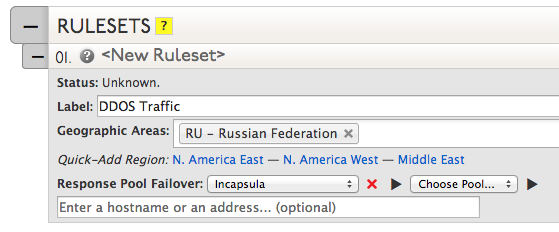
| 10. Rulesets define which Response Pools will respond when a DNS inquiry is made from specific geographic locations.
Under Rulesets, click Create Ruleset and enter a label. In this case, we’ll be creating a rule that will serve the DDOS Traffic Response Pool’s A record when a DNS inquiry is made from Russia. We will call this Ruleset “Incapsula”. In the Geographic Areas field, select the geographic regions you would like the Response Pool to serve, in this case, Russian Federation. Beside Response Pool Failover, select your primary Response Pool (DDOS Traffic) from the drop-down menu. Click Save. |
 |
| 11. Repeat step 10 to create a Ruleset for the rest of your traffic with the Geographic Areas field left blank and the Response Pool Failover set to “Normal Traffic”.
Click Save. |
|
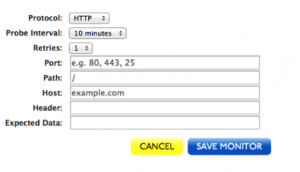
| 12. If desired, you can set up a probe that will monitor the responsiveness of your node and will notify you if one of your nodes goes down.
Beside Monitors, click Create Monitor. Select a monitoring protocol (HTTP, HTTPS, PING, SMTP, or TCP), set the Probe Interval to the desired length of time between probes, the number of Retries before the probe officially considers the server down, and the fill out out the following fields as needed. Then select a notifier from the Monitor Notifiers drop-down menu. Click Save. |
 |
| 13. Once all conditions have been set and saved, click Publish. | |
Configuration Overview